It only takes one hacked email during a property sale in Australia to lose hundreds of thousands. Cybersecurity isn’t optional, it’s financial protection. Recently, seesawing property prices and clever scammers have become a lethal combination: buyers end up wiring deposits to criminals, not conveyancers. This is Business Email Compromise (BEC), not theory, but a real-world threat. Here’s how it unfolds, and what you can do about it.
The Real Threat in Plain Sight
Australian authorities, including the Australian Cyber Security Centre (ACSC), flag an upward trend in real estate-related BEC, especially payment redirection scams where hackers hijack email conversations to reroute funds at exactly the wrong moment.
Between 2021 and early 2022, the Australian Competition and Consumer Commission (ACCC) reported two such scams per week and total losses of $225 million and those are just the reported cases Mondaq. One particularly devastating instance saw a Queensland couple lose $250,000 when the scammers altered their conveyancer’s email just before settlement, stealing their deposit.
Step-by-Step Breakdown (Based on the Cyber Kill Chain)
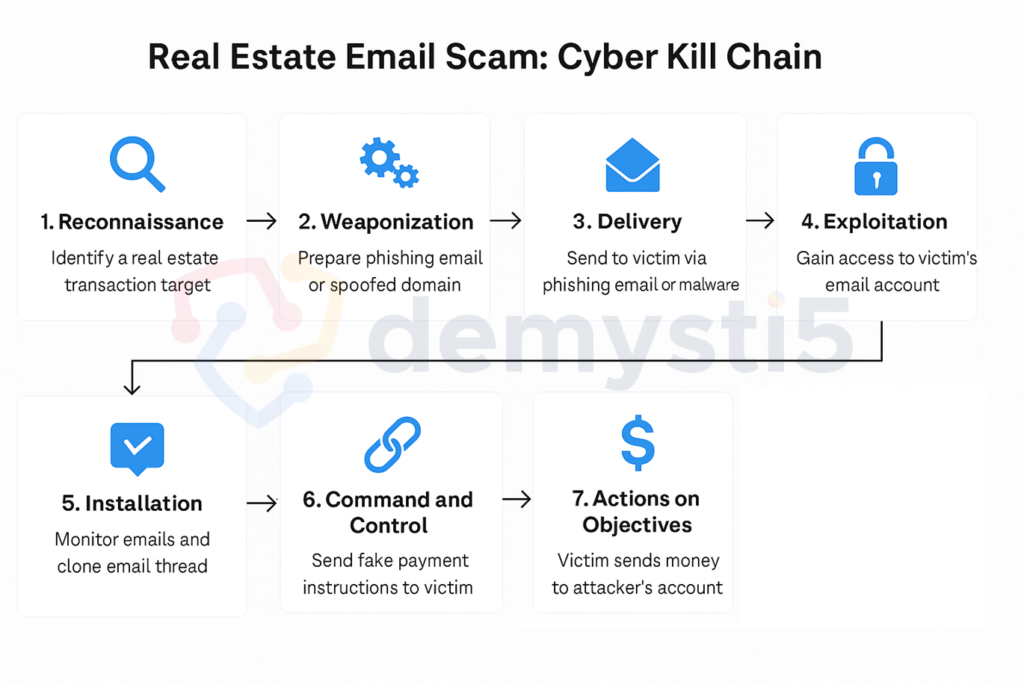
- Reconnaissance (Scouting for Targets)
Cybercriminals begin by identifying potential high-value property transactions. This could be via real estate listing sites, LinkedIn profiles of agents, or social media posts from buyers. They look for patterns like email addresses, agencies, and conveyancing timelines.
Think of this as digital stalking: watching, collecting, and waiting for the right moment. - Weaponization (Building the Attack Tools)
The attacker prepares a phishing email, malicious attachment, or a spoofed domain that mimics a trusted party (like the real estate agent or conveyancer). These are crafted to either:- Steal email credentials
- Drop malware to gain access to the email inbox or device
This might involve free tools like Evilginx or malware kits like Agent Tesla or RedLine Stealer used to harvest inbox contents silently.
- Delivery (Getting In)
The crafted attack is delivered to the victim via:- Phishing emails pretending to be clients or banks
- Malicious PDFs claiming to be contracts or settlement info
- In some cases, hijacking unsecured Wi-Fi or exploiting outdated email clients
Once clicked, the attacker gains access to the email account or device.
- Exploitation (Email Access and Control)
Now inside the inbox, the attacker doesn’t cause chaos, they silently observe:- They set up auto-forwarding rules to copy future emails
- They mark real agent emails as “read” and craft replies
- They clone the thread, using almost identical domain names (e.g. [email protected] vs [email protected])
- Installation (Maintaining Access)
The attacker may install further malware or persist via OAuth token hijacking. This lets them keep accessing the email even if passwords are changed, particularly dangerous if 2FA is not in place. - Command and Control (Taking the Lead)
They now direct the flow of conversation. Right before the property settlement (when emotions and urgency are high), they send a final instruction: “Please send the balance to the updated trust account: BSB 123-456, Acc No. 567890123, note the change is urgent due to audit rules.” The email looks identical to previous ones, sent from the same thread, and often carries a spoofed signature and branding. - Actions on Objectives (The Heist)
Once the victim wires the money, the attackers either:- Transfer it through multiple “money mule” accounts
- Convert it to crypto
- Cash out before anyone notices
In most cases, by the time fraud is suspected, the money is gone irreversibly.
Key Security Observations:
- These scams rarely exploit bank systems, they exploit human behavior and email trust.
- The attacker’s primary goal is not disruption, but stealth and timing.
- Even legitimate emails (like PDF contracts) can be faked to manipulate buyers.
- The entire operation, from targeting to payout can be automated using off-the-shelf malware kits and Telegram-based data marketplaces.
Why the Scam Works So Well
- Email trust: People assume legit emails are secure.
- Transaction volume: Real estate deals involve large sums so they are perfect targets.
- Timing pressure: Settlements often happen on tight deadlines, leaving little time for verification.
- Low reversal rate: Lost funds are rarely recoverable via the banking system.
- Multiple vulnerable parties: Agents, lawyers, banks, and homebuyers can all be points of failure.
So What Can You Do About This
Here are some actionable advice you can follow before and during the sale.
Before the Sale:
- Use Secure Email Domains: Where possible, request your real estate agent and conveyancer to use business-grade email accounts (like Microsoft 365 with MFA) instead of free Gmail/Yahoo accounts.
- Set Expectations Early: During initial meetings, agree on one channel (e.g., in-person, Email, or verified phone number) for confirming payment instructions.
- Request an “Out-of-Band Verification Policy”: Ensure that all parties: agent, buyer, seller, conveyancer agree to verify any changes to bank details via a phone call not initiated via email.
During the Sale:
Use this checklist at the point where money is about to be transferred:
- Verify Account Details Twice With Two Sources: Always confirm bank account numbers over a phone call using a number you sourced independently (e.g., business card, official website), not from an email.
- Ask for a Dummy Transfer: Instead of transferring the full amount, send $1 and confirm it was received before transferring the full sum. A small delay is better than a large loss.
- Use Encrypted Email Extensions or Secure Portals: Ask your conveyancer if they use secure document exchange platforms (like DocuSign, Settl, or Infotrack). Encourage it.
- Check Email Headers and Metadata: If you’re technical or have someone who is, or use Demysti5 Advice Section to check if recent emails show any signs of spoofing or email relay inconsistencies.
- Cross-Check Email Thread Consistency: Look for odd formatting changes in signature blocks, domain name typos (e.g., realestat3.com.au), or sudden tone changes. These are subtle signs of a hijacked thread.
- Don’t Act on Urgency Alone: Most fraud emails create urgency. Pause. Call. Think. Especially if they say “transfer must be made within the next 1 hour.”
- Always Use Two-Factor Authentication (2FA): Make sure your own email account has 2FA turned on, especially if you’re the buyer or seller. It’s your most exposed entry point.
👉 Click here to download the Secure Property Sale Checklist (PDF)
When in Doubt: Call, Don’t Click
The number one defense is talking to a human you trust. Email is a powerful tool for communication but in high-stakes money transfers, it’s also your biggest risk.
Even if an email looks perfect, pause and verify using a phone call or secure in-person meeting before sending money.
Scams like these aren’t just stories in the news, they’re happening more often, and often quietly. Taking small but deliberate steps can make a big difference. It’s not about paranoia, it’s about staying a step ahead.
Want to dive deeper into personal online safety? Demysti5 offers tailored guides and tools for everyone—from parents and families, students, and senior citizens to remote workers, job seekers, and high net worth individuals.
You can also:
- Check your Online Safety Score
- Get practical Cyber Advice
- Adopt Secure Habits to protect your digital life
- Explore Cyber Safety for Business and Colleges
- Spread the Word to help others stay secure
- Read the latest on the Demysti5 Blog
- Access the Web App to track your cyber safety progress and complete personalized tasks
- Download the Android App or get it on Google Play
- Follow Demysti5 on Facebook and YouTube
Stay informed. Stay protected. Demysti5 it.





